Trello Power-Up Security: XSS
Posted On: 2024-02-10
TLDR: Use t.safe()
By far, the most common type of vulnerability ticket I’ve seen when it comes to Power-Ups is XSS. At the time of writing and according to the OWASP Top Ten, XSS remains one of the top security risks of web applications.
Trello provides a lot of accessible data for third-party Power-Ups: cards, lists, comments, etc.
Having a lot of data at your disposal is great, but also poses a lot of potential areas of risk in your application!
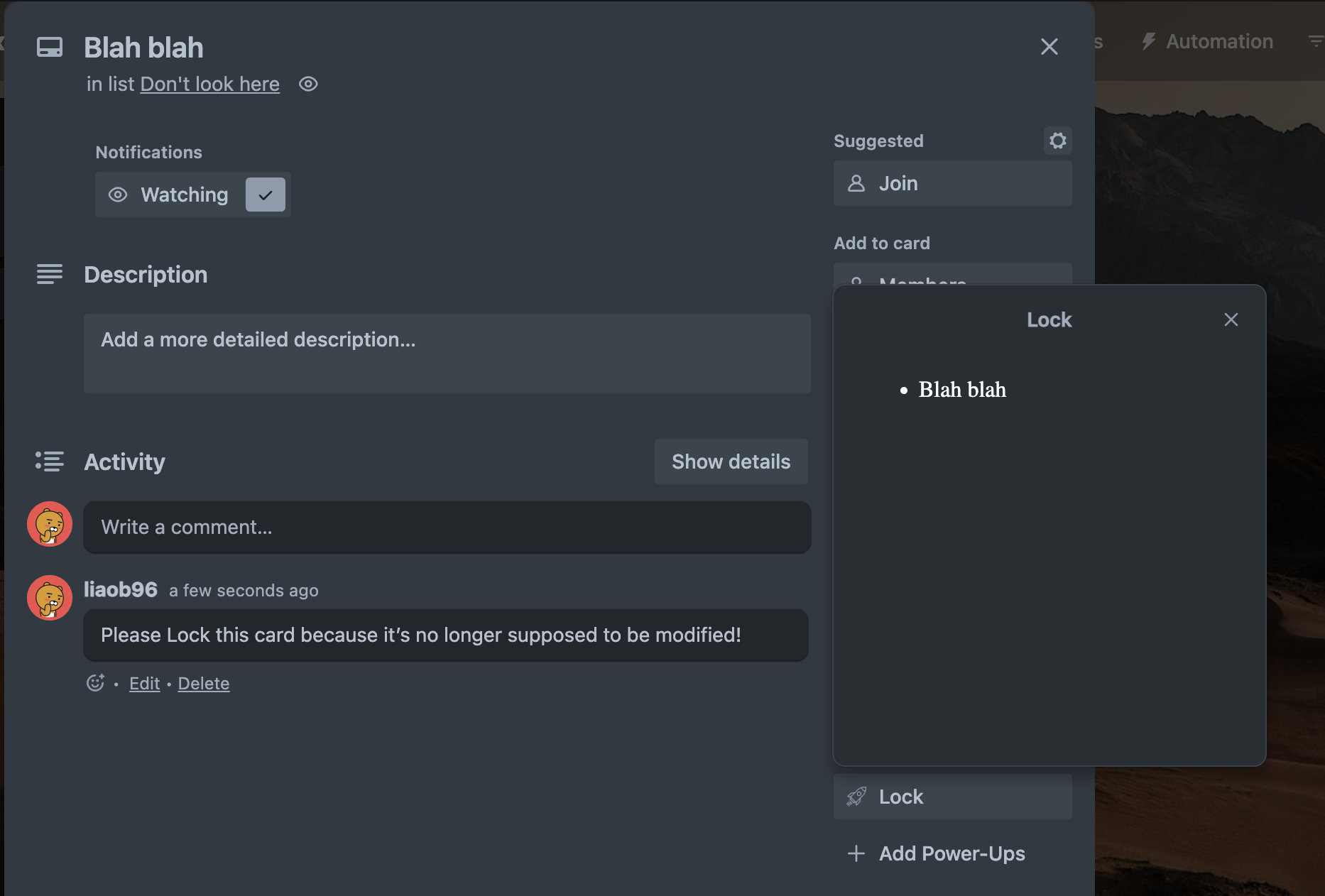
Example: Here I have a simple Power-Up with a Card Button that tracks which cards it was pressed from:
I’m using the Power-Up library to grab card names and pass them into my iframe, rendering them as list items:
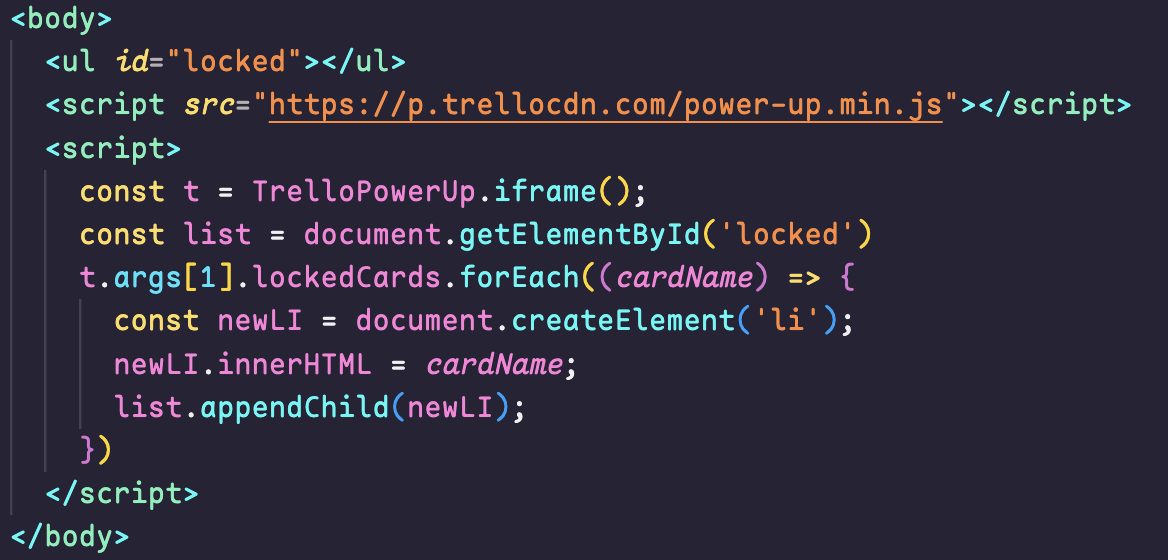
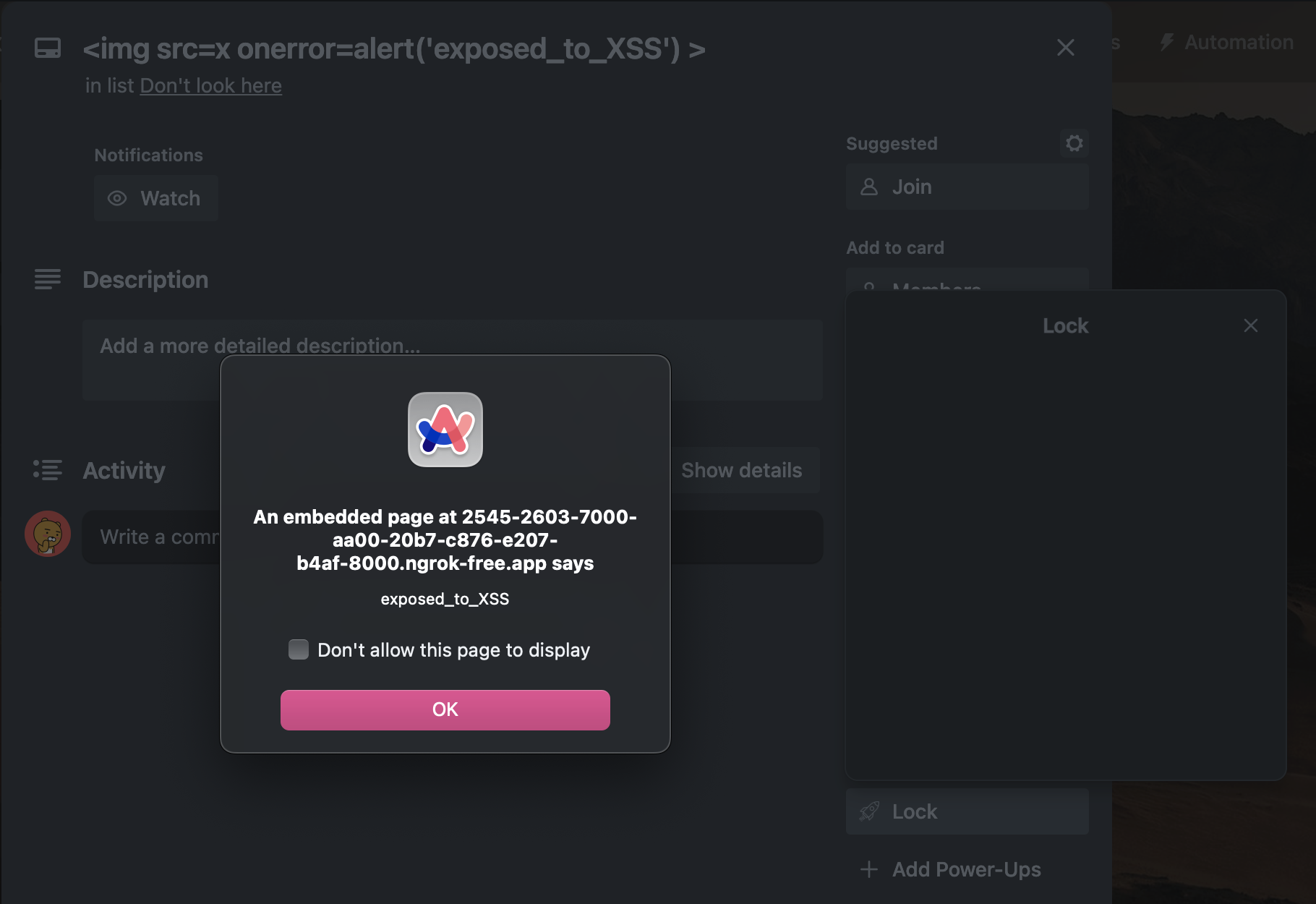
Between my direct use of card names and using innerHTML in my list item elements, this is vulnerable to some Stored XSS!
As a simple solution, we can use the readily available t.safe() function around text that’s user input and avoid any unfortunate surprises!
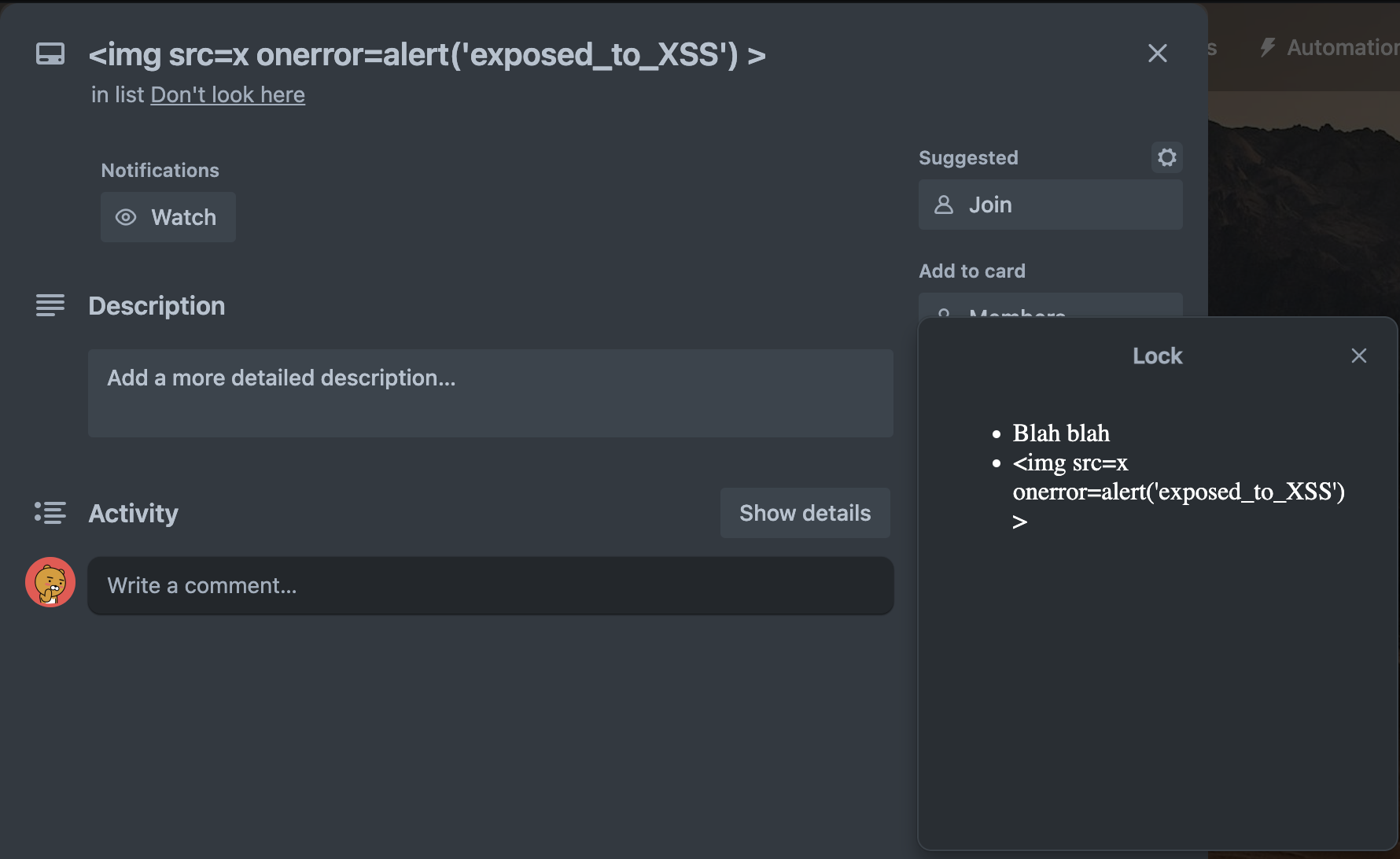
Nice.